The rollout of 5G networks is revolutionizing the way we connect to the internet, offering faster speeds, lower latency, and a vastly improved experience for users and businesses alike. However, with these advancements come new challenges in the realm of cybersecurity. As the adoption of 5G accelerates, it is essential to understand the risks it introduces and how individuals, businesses, and governments can safeguard their systems from potential cyber threats.
In this post, we will explore the relationship between 5G and cybersecurity, highlighting the key vulnerabilities that arise with the deployment of 5G, the potential threats, and best practices for protecting against cyberattacks in a 5G-enabled world.
1. What is 5G and How Does It Differ from Previous Generations?
Before diving into the cybersecurity aspects, it is important to understand what 5G is and how it compares to previous network generations (e.g., 4G, 3G). This section will cover:
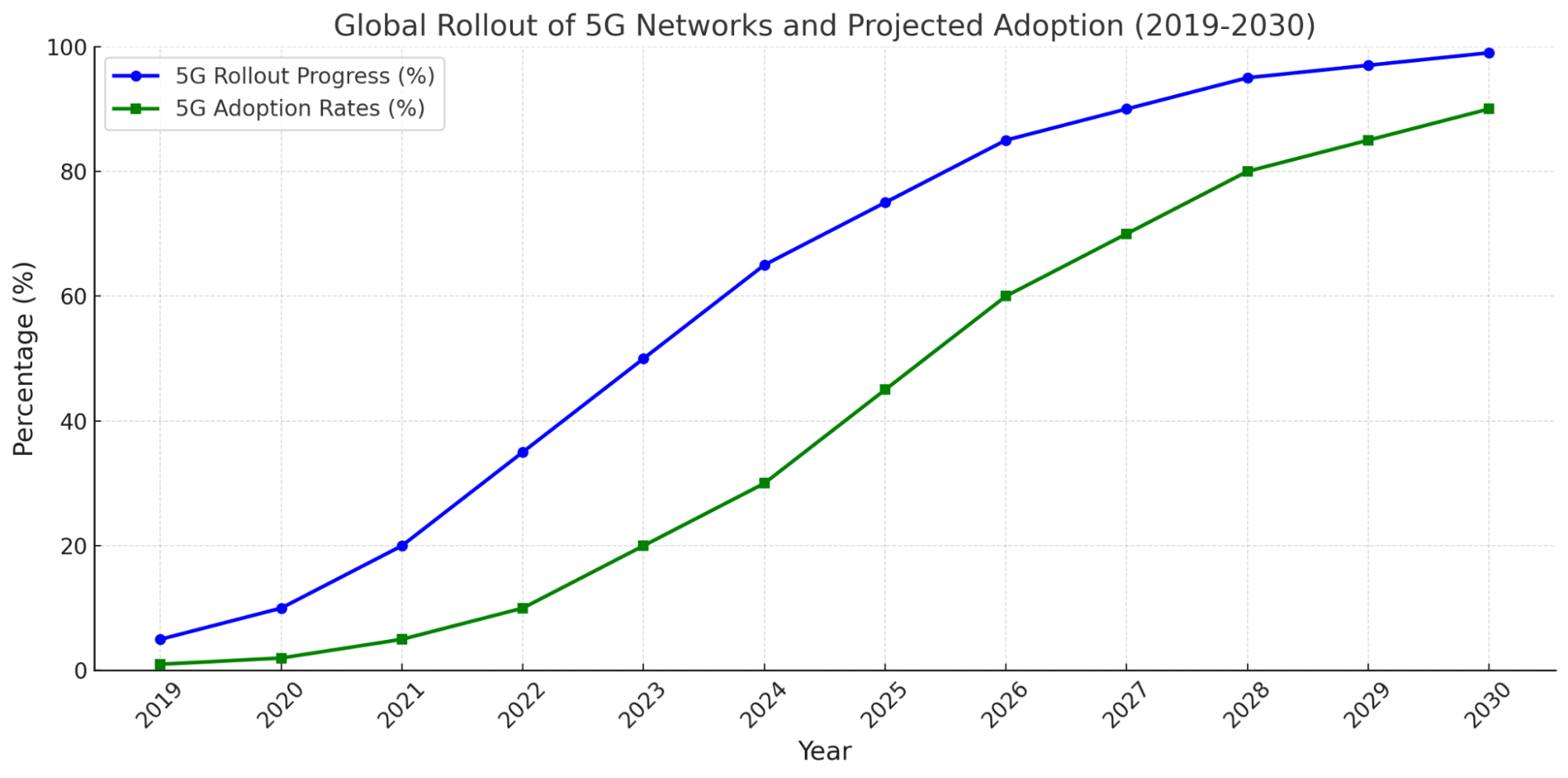
- Speed and Latency: 5G promises to be up to 100 times faster than 4G, with significantly lower latency (around 1ms). This makes real-time applications, such as autonomous vehicles and telemedicine, possible.
- Capacity and Connectivity: 5G can handle a higher density of devices per square kilometer, enabling the massive IoT (Internet of Things) ecosystem.
- Network Slicing: A feature unique to 5G, allowing operators to create customized virtual networks for specific applications (e.g., low-latency for autonomous vehicles, high-speed for video streaming).
| Feature | 3G | 4G | 5G |
|---|---|---|---|
| Speed | Up to 42 Mbps | Up to 1 Gbps | 10 Gbps or higher |
| Latency | ~100 ms | ~30-50 ms | ~1 ms |
| Device Density | 100,000/km | 1,000,000/km² | 1,000,000+/km² |
| Use Cases | Voice calls, basic data | HD streaming, gaming | Autonomous systems, IoT |
2. The New Cybersecurity Threat Landscape with 5G
With the proliferation of 5G, new cybersecurity risks and vulnerabilities are emerging. This section will discuss:
- Increased Attack Surface: 5G networks support billions of connected devices, from smartphones to sensors and industrial machines. Each new device introduces a potential point of vulnerability.
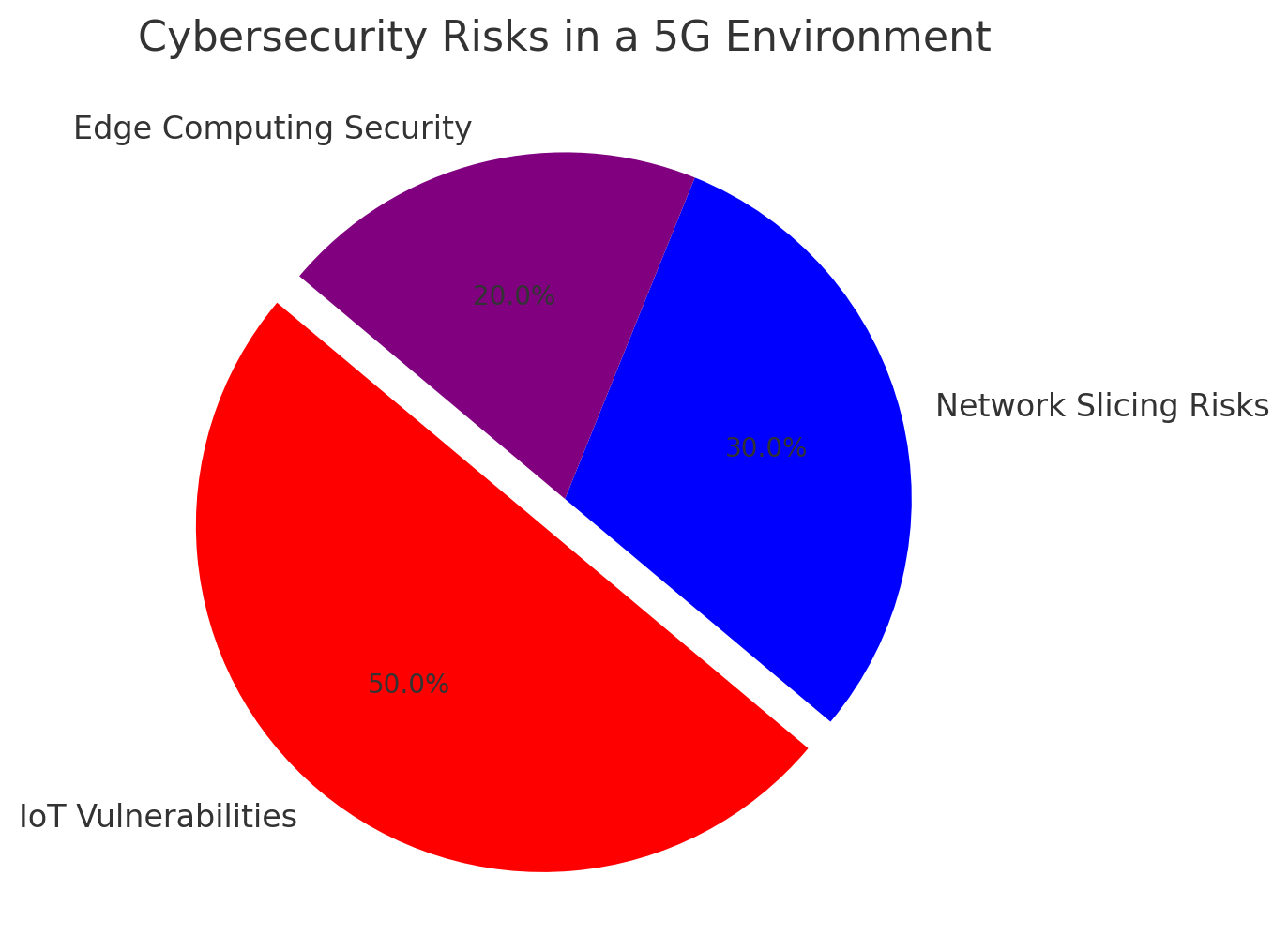
- IoT Vulnerabilities: The rise of 5G will dramatically expand the IoT, which often suffers from poor security. A large number of IoT devices are designed with minimal security protocols, making them an attractive target for hackers.
- Network Slicing Risks: While network slicing allows for customized virtual networks, it also introduces the risk of misconfigured slices, which could allow hackers to infiltrate a particular slice and gain access to critical data or systems.
- Cloud and Edge Computing: 5G will push more data processing to the edge of the network, often outside the direct control of organizations. This opens new doors for cybercriminals to exploit weak edge security.
3. Key Cybersecurity Challenges in 5G Networks
This section will examine some of the most critical cybersecurity challenges posed by 5G networks:
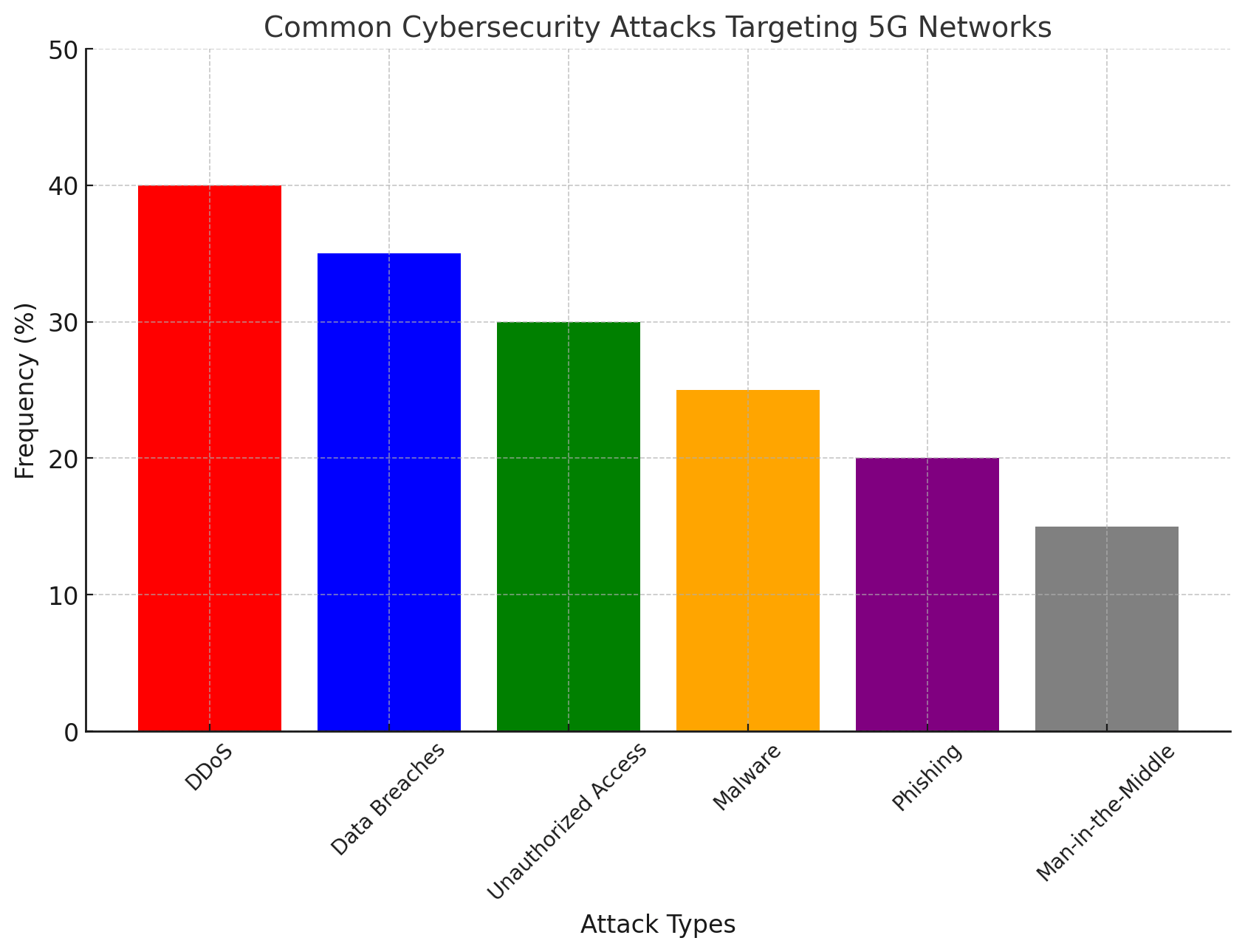
- Encryption Weaknesses: While 5G supports encryption, not all devices are equipped to handle strong encryption, leaving them susceptible to data breaches.
- Supply Chain Risks: 5G involves many components from different vendors, increasing the risk of malicious actors exploiting vulnerabilities in hardware or software supplied by third parties.
- DDoS Attacks: With the increased number of connected devices, 5G networks are more susceptible to Distributed Denial of Service (DDoS) attacks, which can overwhelm network resources and cause massive outages.
- Unauthorized Access: The complexity of 5G networks and their integration with legacy systems can make it easier for hackers to gain unauthorized access.
4. Best Practices for Securing 5G Networks
Securing a 5G network is not only about identifying vulnerabilities but also implementing robust security practices to mitigate potential threats. This section will outline the best practices for securing 5G networks:
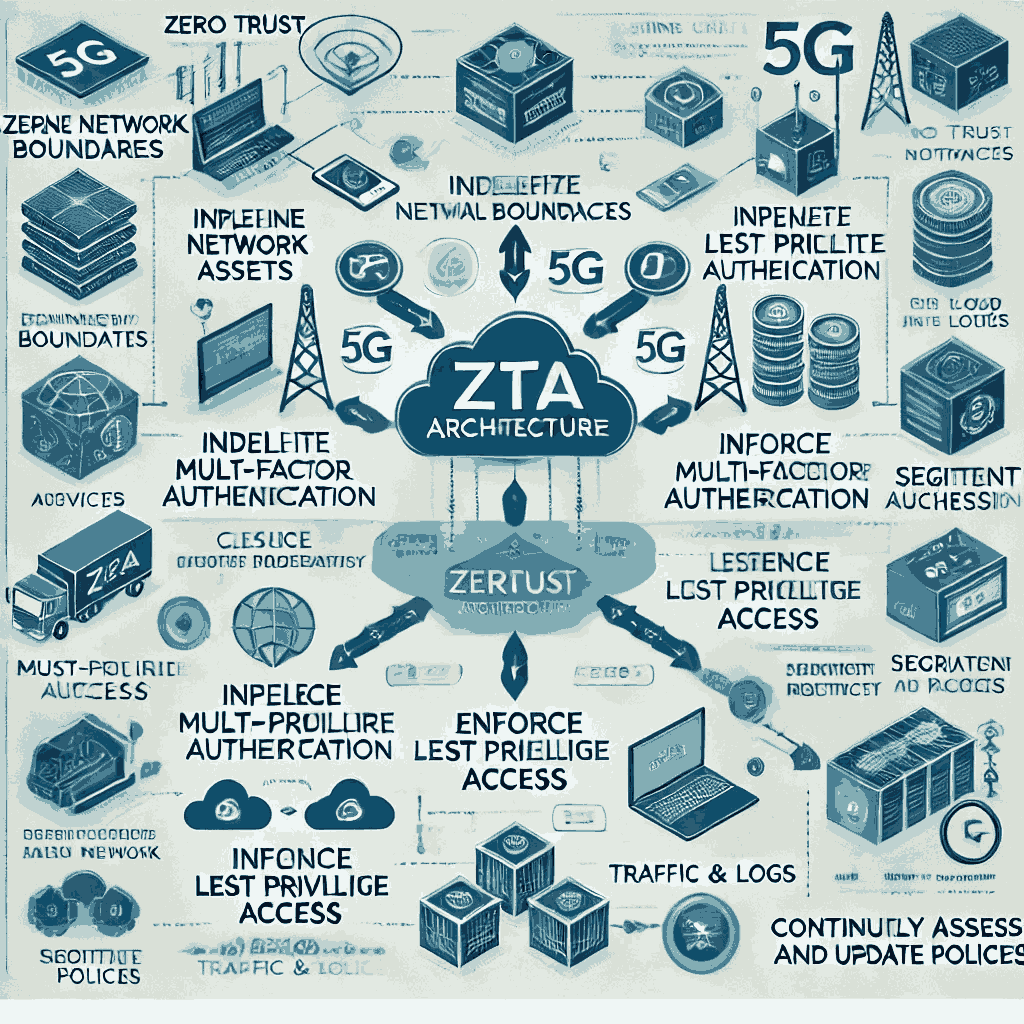
- End-to-End Encryption: Ensuring that all data transmitted across 5G networks is encrypted end-to-end to prevent interception or unauthorized access.
- Zero Trust Architecture: Adopting a Zero Trust security model, where devices, users, and applications are continuously verified before being granted access to network resources.
- Regular Software and Firmware Updates: Ensuring that IoT devices and other 5G-connected systems are kept up to date with the latest security patches.
- Multi-Factor Authentication (MFA): Implementing MFA to add an extra layer of security when accessing sensitive data or systems on the network.
- Artificial Intelligence (AI) for Threat Detection: Using AI-powered tools to monitor network traffic in real-time, detecting anomalies that may indicate a cybersecurity breach.
5. Government Regulations and Industry Standards for 5G Security
Governments and industry organizations are actively working to create standards and regulations for securing 5G networks. This section will discuss:
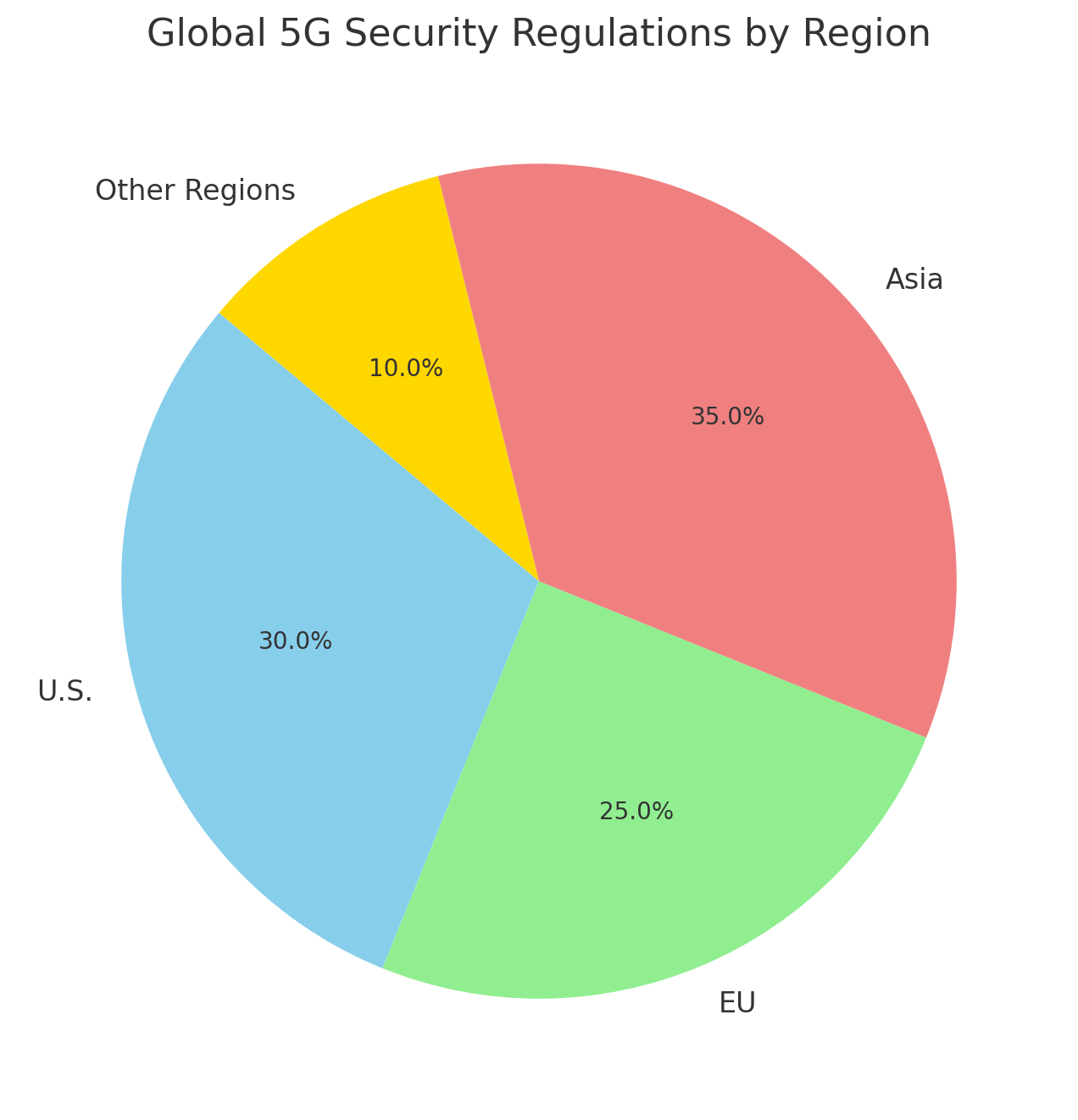
- National Security Concerns: Governments around the world are concerned about the potential for foreign adversaries to exploit 5G networks for espionage or cyberattacks.
- Regulatory Bodies and Standards: Industry standards, such as those from the 3rd Generation Partnership Project (3GPP), the National Institute of Standards and Technology (NIST), and the European Union Agency for Cybersecurity (ENISA), provide guidelines for securing 5G networks.
- Collaboration between Private and Public Sectors: Governments and private sector organizations must collaborate to create secure 5G infrastructures, as seen in initiatives such as the Open RAN (Radio Access Network) project, which promotes open-source solutions to improve transparency and security.
- Multi-Factor Authentication (MFA): Implementing MFA to add an extra layer of security when accessing sensitive data or systems on the network.
- Artificial Intelligence (AI) for Threat Detection: Using AI-powered tools to monitor network traffic in real-time, detecting anomalies that may indicate a cybersecurity breach.
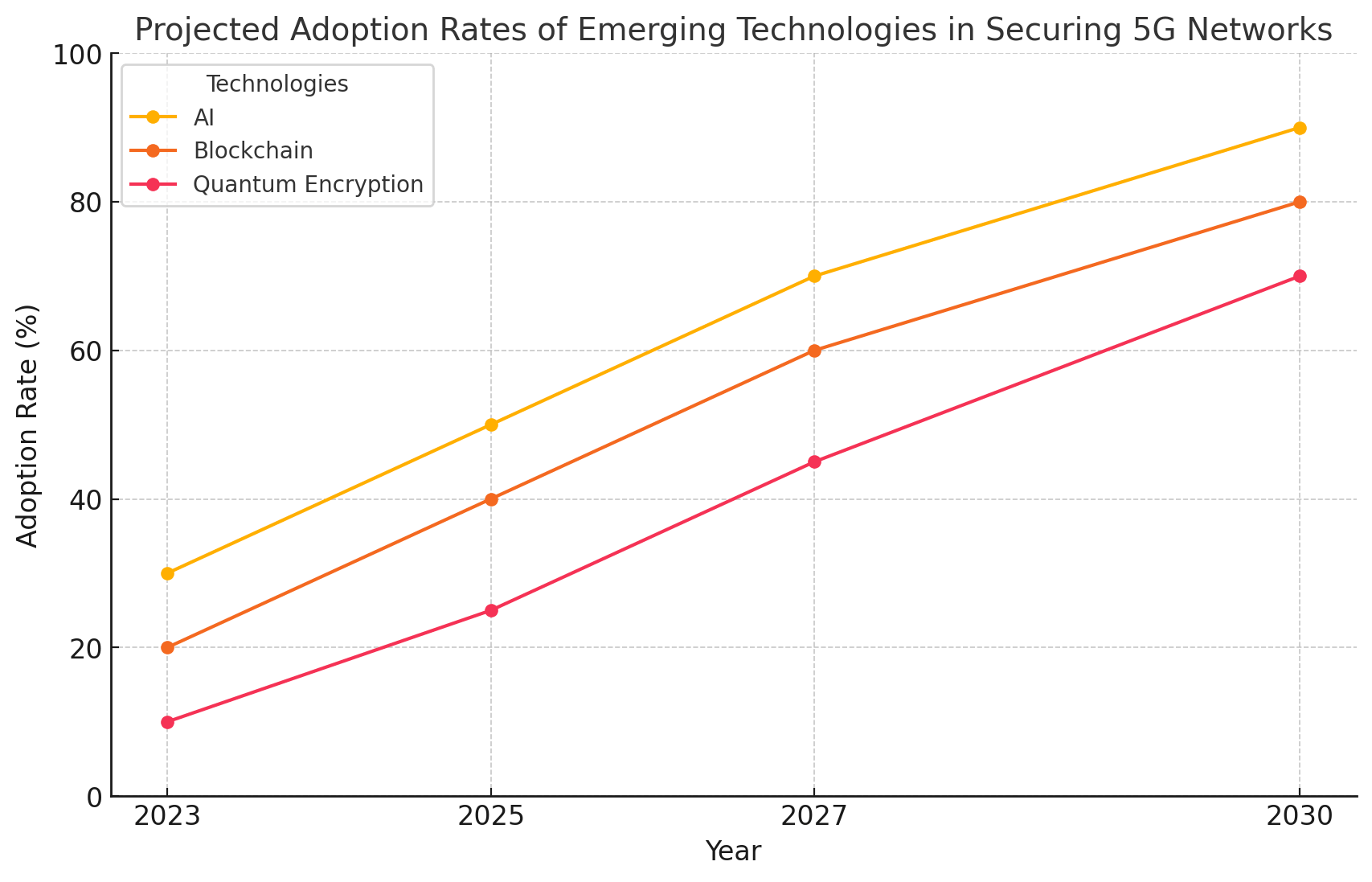
6. Emerging Technologies in 5G Security
As 5G technology evolves, so too do the security tools and technologies designed to protect it. This section will discuss emerging technologies and innovations in 5G security:
- Blockchain for 5G Security: Blockchain’s decentralized nature can be used to enhance the security of 5G networks by ensuring the integrity of data and preventing tampering.
- AI-Powered Security Solutions: AI algorithms can detect unusual patterns of behavior and predict potential threats before they happen, providing proactive protection for 5G networks.
- 5G Security Automation: Automating security protocols, such as incident response and threat hunting, using AI and machine learning can drastically improve the speed and effectiveness of 5G network protection.
- Quantum Computing and Encryption: As quantum computing advances, it will introduce new forms of encryption that are resistant to attacks from both classical and quantum computers.
7. Case Studies: Real-World Cybersecurity Threats and Solutions in 5G
In this section, real-world case studies of cybersecurity threats and solutions related to 5G networks will be analyzed:
Case Study 1:
- 5G IoT Vulnerability Exploits: A look at how hackers targeted 5G-connected IoT devices in a recent attack, how the vulnerability was exploited, and what measures were taken to mitigate the risk.
| Case Study | Key Threats | Solutions | Outcomes |
|---|---|---|---|
| Telecom Provider A | DDoS attacks, unauthorized access | Zero Trust Architecture, AI-based detection | 95% reduction in unauthorized access incidents |
| Telecom Provider B | Data breaches from network slicing | End-to-end encryption, blockchain | Enhanced data integrity and reduced breach risk by 70% |
| Telecom Provider C | IoT device vulnerabilities | Regular updates, secure boot | 80% decrease in IoT-related security issues |
Case Study 2:
- DDoS Attacks on 5G Networks: A large-scale DDoS attack on a 5G network that crippled service for millions of users. What steps were taken to combat the attack and prevent future incidents?
| Case Study | Key Threats | Solutions | Outcomes |
|---|---|---|---|
| Smart City X | Real-time data manipulation | AI-based real-time monitoring | Improved threat detection response time by 60% |
| Enterprise Y | Tampering of sensitive transactions | Blockchain-based smart contracts | Fully tamper-proof transactions with 0 reported cases of fraud |
| Government Agency Z | Insider threats and lack of transparency | AI-driven access management, blockchain audit trails | 50% improvement in system transparency |
Case Study 3:
- Regulatory Response to 5G Security Breaches: How governments have responded to security breaches involving 5G networks and the lessons learned from these incidents.
| Industry | Key Threats | Solutions | Outcomes |
|---|---|---|---|
| Healthcare | Ransomware attacks on connected devices | Endpoint protection, network segmentation | Reduced ransomware incidents by 40% |
| Manufacturing | Supply chain cyber-attacks | Blockchain for supply chain security | Secure tracking with improved traceability by 80% |
| Financial Services | Phishing and fraudulent transactions | AI for fraud detection | Real-time fraud detection with a 90% success rate |
Conclusion: Staying Safe in the 5G Era
As 5G networks continue to roll out and reshape the digital landscape, businesses, governments, and individuals must be proactive in addressing cybersecurity risks. The rise of connected devices, network slicing, and cloud-based solutions in 5G opens new opportunities, but also exposes new vulnerabilities. By implementing best practices, adopting new security technologies, and staying informed about emerging threats, we can ensure that the promise of 5G is realized securely.
FAQs
5G is the fifth generation of mobile network technology, offering faster speeds, lower latency, and the ability to connect more devices simultaneously compared to previous generations like 4G and 3G. 5G utilizes higher frequency bands, improved network architectures, and advanced technologies like beamforming, making it ideal for applications like the Internet of Things (IoT) and real-time communication.
While 5G brings significant benefits, it also introduces new cybersecurity challenges. These include a larger attack surface due to increased device connectivity, more complex network architecture, and the reliance on software-defined infrastructure, which could make it vulnerable to cyberattacks. Additionally, 5G networks involve third-party vendors, potentially increasing the risk of supply chain attacks.
5G's ability to support a massive number of connected devices will drive the growth of IoT, but it also exposes IoT devices to greater security risks. With billions of devices interacting over 5G networks, attackers may target vulnerable devices to gain access to sensitive data or disrupt services. Enhanced security protocols and encryption methods will be necessary to safeguard IoT ecosystems.
Organizations can take several measures to secure their networks in the 5G era, including adopting end-to-end encryption, using advanced authentication protocols, and investing in secure network architecture. They should also prioritize threat detection and response strategies, conduct regular vulnerability assessments, and stay up to date with evolving security standards to mitigate potential risks associated with 5G deployment.





