Introduction
Have you ever wondered how secure your digital assets are in the rapidly evolving Web3 landscape? As blockchain technology continues to revolutionize industries, the security risks associated with digital assets have also increased. Cybercriminals are constantly innovating new ways to breach security, making it essential for individuals and businesses to stay ahead with robust security measures.
At True Value Infosoft, we recognize the importance of security in the digital age. As the best app development company in India, we specialize in providing cutting-edge solutions that protect digital assets from cyber threats. Whether it's securing smart contracts, safeguarding crypto wallets, or implementing multi-layered authentication protocols, our expertise ensures that businesses can navigate Web3 with confidence.
Common Threats in Web3
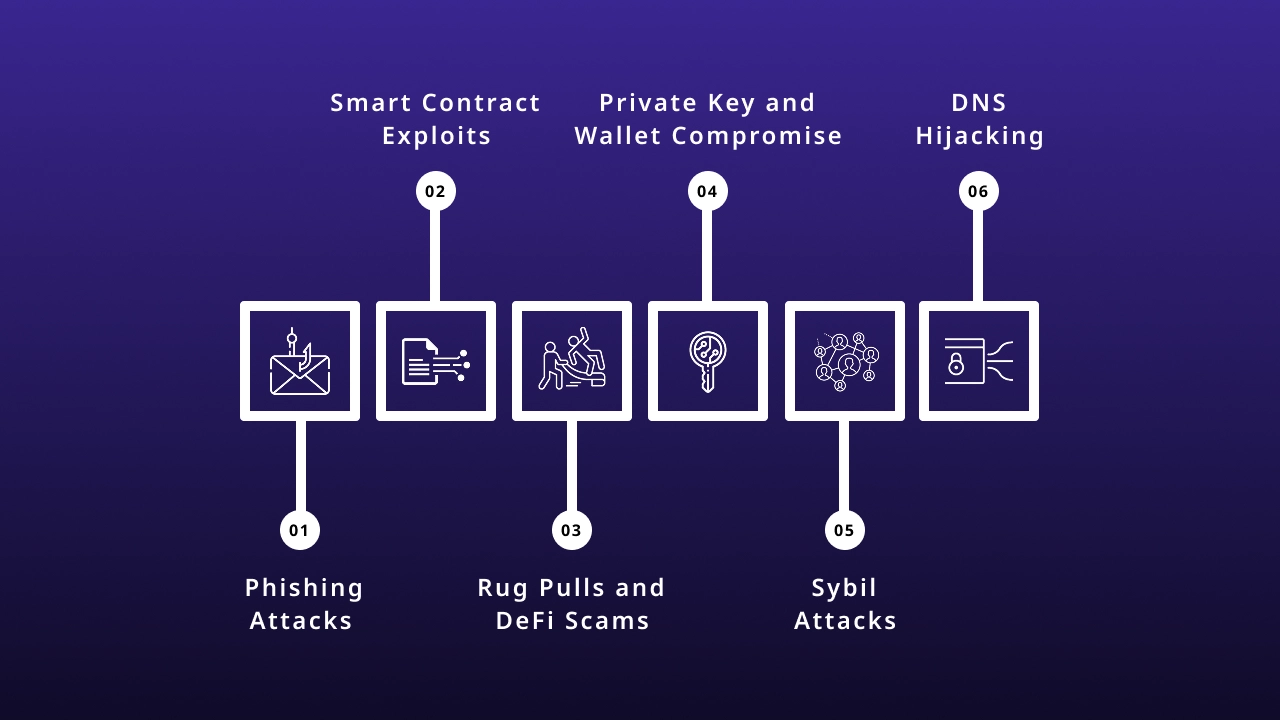
1. Phishing Attacks
Phishing remains a primary attack vector in Web3, where attackers trick users into revealing private keys or signing malicious transactions. This can occur through:
- Fake websites imitating genuine platforms
- Malicious browser extensions
- Social engineering via emails or direct messages
2. Smart Contract Exploits
Smart contracts are self-executing codes on the blockchain. Vulnerabilities in these contracts can lead to exploits such as:
- Reentrancy attacks: Repeated function calls that drain funds
- Integer overflows: Exploiting computational errors
- Logic flaws: Faulty contract logic leading to unintended behavior
3. Rug Pulls and DeFi Scams
Fraudulent projects attract investments and then disappear, leaving investors with worthless tokens. Scams include:
- Exit scams: Developers abandon projects after raising funds
- Pump-and-dump schemes: Artificial price inflation before mass liquidation
- Fake liquidity pools: Manipulated liquidity to deceive investors
4. Private Key and Wallet Compromise
Losing private keys means losing access to digital assets. Threats include:
- Malware or keyloggers stealing private keys
- Weak seed phrase storage
- Compromised hardware wallets
5. Sybil Attacks
Attackers create multiple fake identities to manipulate network operations, such as consensus mechanisms or governance voting.
6. DNS Hijacking
Web3 projects often rely on decentralized domain names (ENS, Unstoppable Domains). Attackers can hijack domain resolution, redirecting users to malicious sites.
Best Practices for Securing Your Wallets and Private Keys
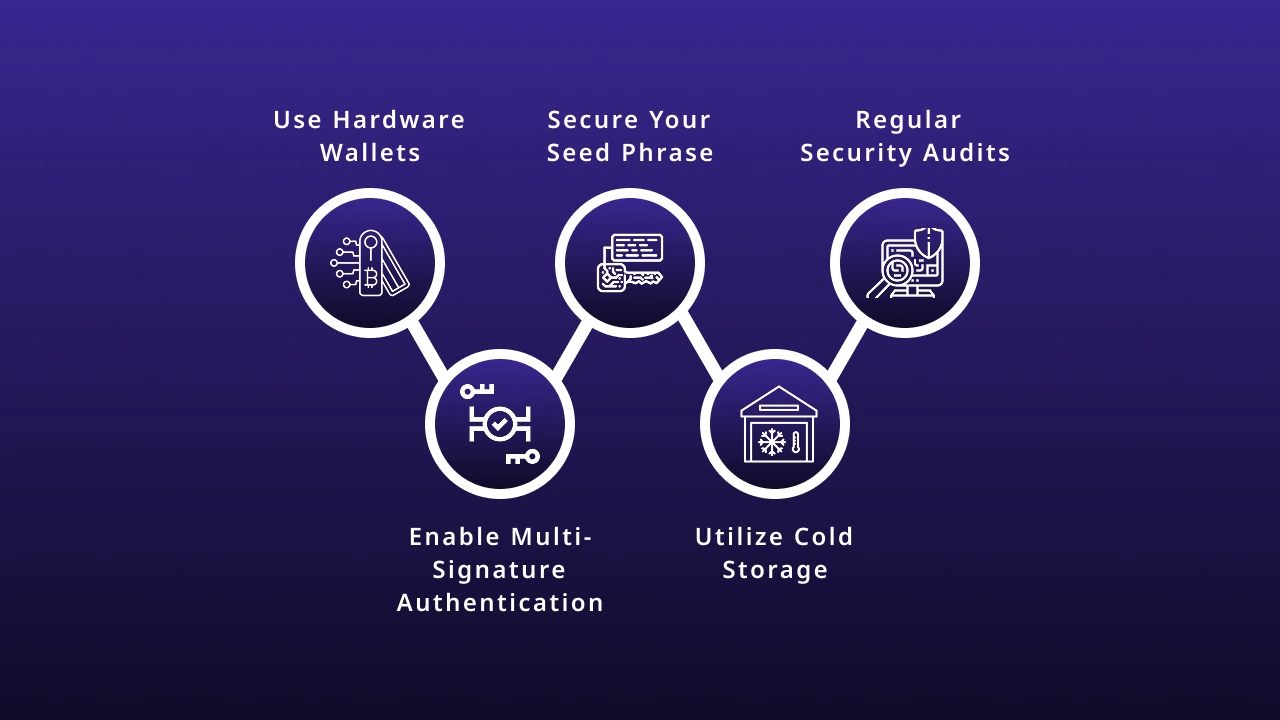
1. Use Hardware Wallets
Hardware wallets like Ledger and Trezor keep private keys offline, making them less susceptible to online attacks.
2. Enable Multi-Signature Authentication
Multi-signature (multi-sig) wallets require multiple approvals before executing transactions, reducing the risk of unauthorized access.
3. Secure Your Seed Phrase
- Store seed phrases offline
- Use fireproof and waterproof storage devices
- Never share your seed phrase with anyone
4. Utilize Cold Storage
For long-term holdings, store digital assets in cold wallets (offline) rather than hot wallets connected to the internet.
5. Regular Security Audits
Regularly audit wallets and smart contracts to identify vulnerabilities before attackers do.
Smart Contract Security and Audit Strategies
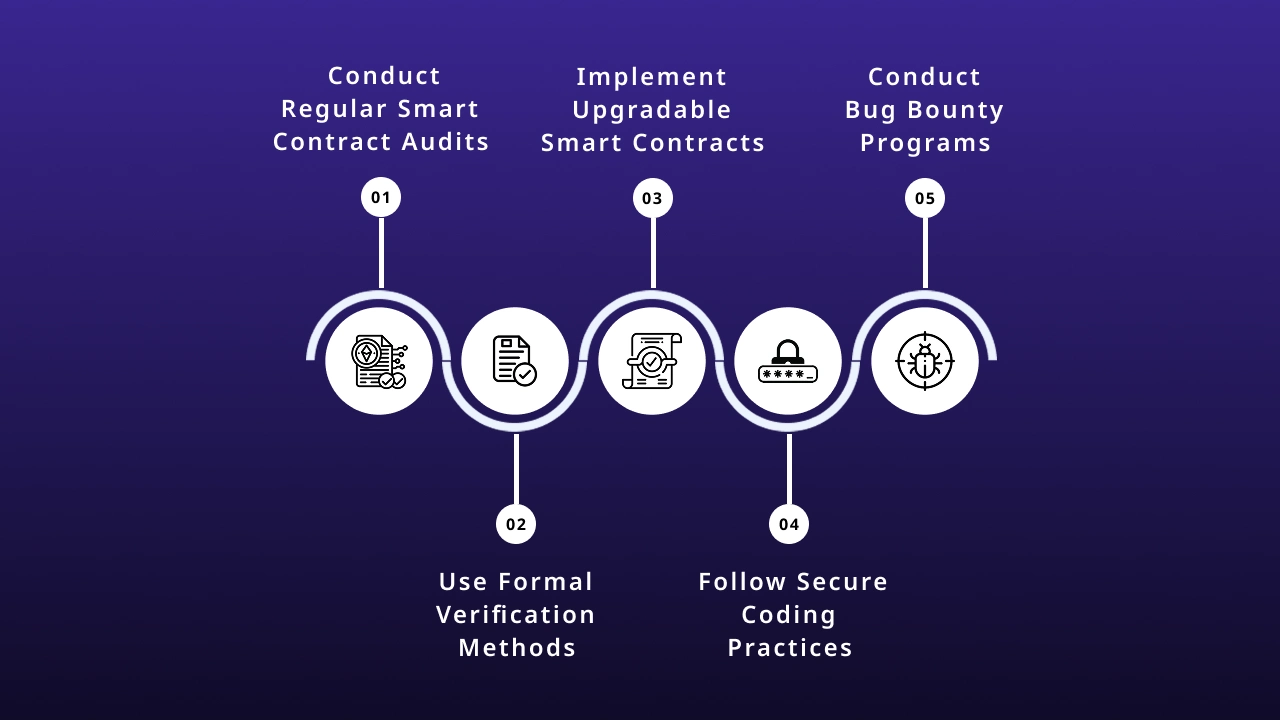
1. Conduct Regular Smart Contract Audits
Hire reputable security firms like CertiK, OpenZeppelin, or Trail of Bits to conduct thorough audits before deploying smart contracts.
2. Use Formal Verification Methods
Formal verification mathematically proves a smart contract’s correctness, minimizing vulnerabilities.
3. Implement Upgradable Smart Contracts
Modular smart contracts allow for bug fixes without requiring a complete redeployment.
4. Follow Secure Coding Practices
- Use established libraries like OpenZeppelin
- Avoid complex code structures
- Implement reentrancy guards
5. Conduct Bug Bounty Programs
Encourage ethical hackers to identify vulnerabilities in exchange for rewards.
Decentralized Identity and Authentication Solutions
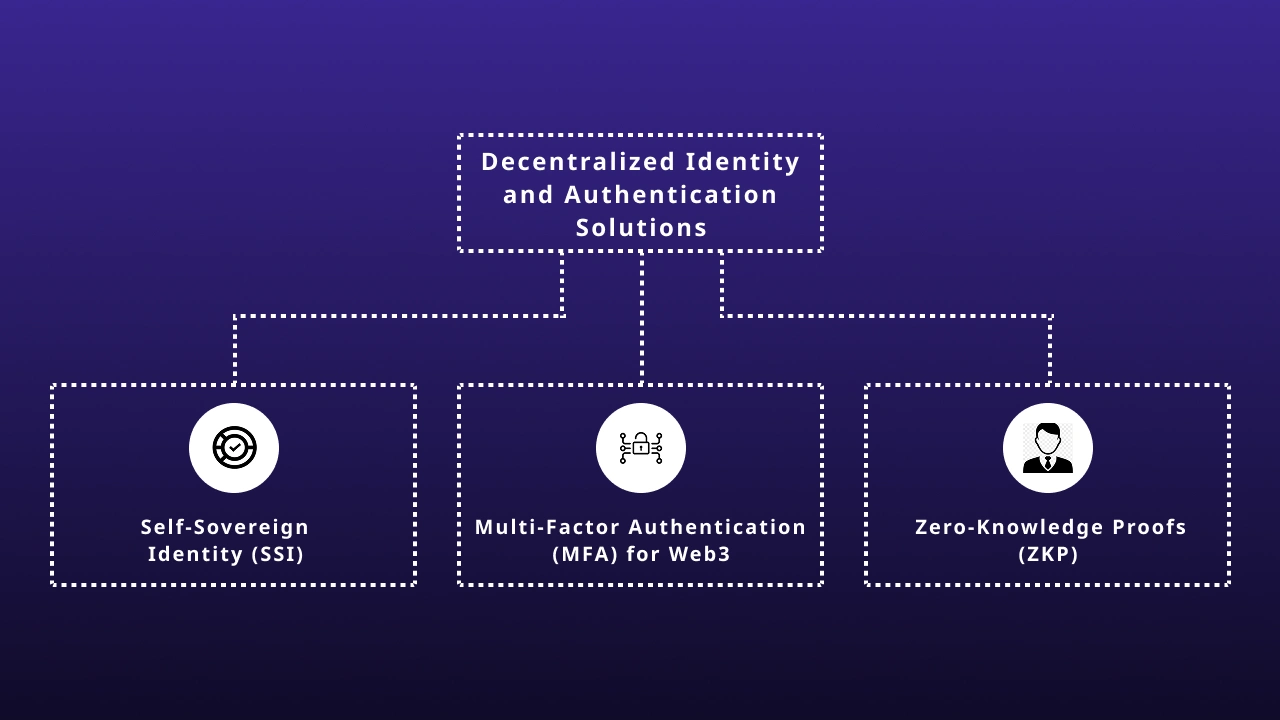
1. Self-Sovereign Identity (SSI)
SSI enables users to control their digital identities without relying on centralized entities. Solutions include:
- Decentralized Identifiers (DIDs)
- Verifiable Credentials (VCs)
2. Multi-Factor Authentication (MFA) for Web3
Combining biometrics, security keys, and decentralized authentication reduces the risk of unauthorized access.
3. Zero-Knowledge Proofs (ZKP)
ZKP allows users to prove information without revealing the data, enhancing privacy in authentication.
The Role of AI and Machine Learning in Web3 Security
AI and ML improve Web3 security by detecting and preventing threats through:
- Anomaly detection: Identifying suspicious transactions in real-time
- Threat intelligence: Predicting attacks based on historical data
- Automated smart contract analysis: Scanning code for vulnerabilities
- Bot detection: Preventing Sybil attacks and fraudulent activities
Regulatory and Compliance Aspects
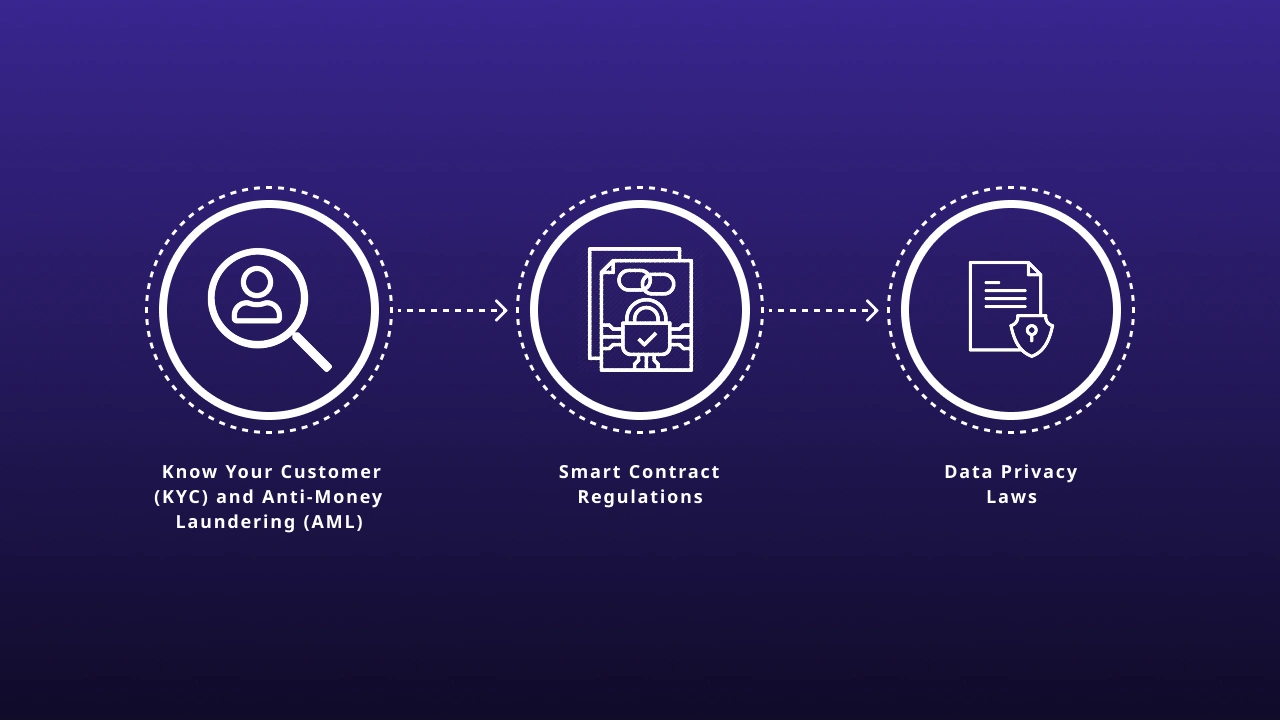
As Web3 adoption grows, governments and regulatory bodies establish guidelines to enhance security and consumer protection.
1. Know Your Customer (KYC) and Anti-Money Laundering (AML)
- Decentralized exchanges (DEXs) integrating compliance measures
- Blockchain analytics firms tracking illicit activities
2. Smart Contract Regulations
- Legal frameworks for liability in case of contract failures
- Auditing standards for security compliance
3. Data Privacy Laws
- GDPR and blockchain compatibility
- User rights over on-chain data
Future Trends in Web3 Security
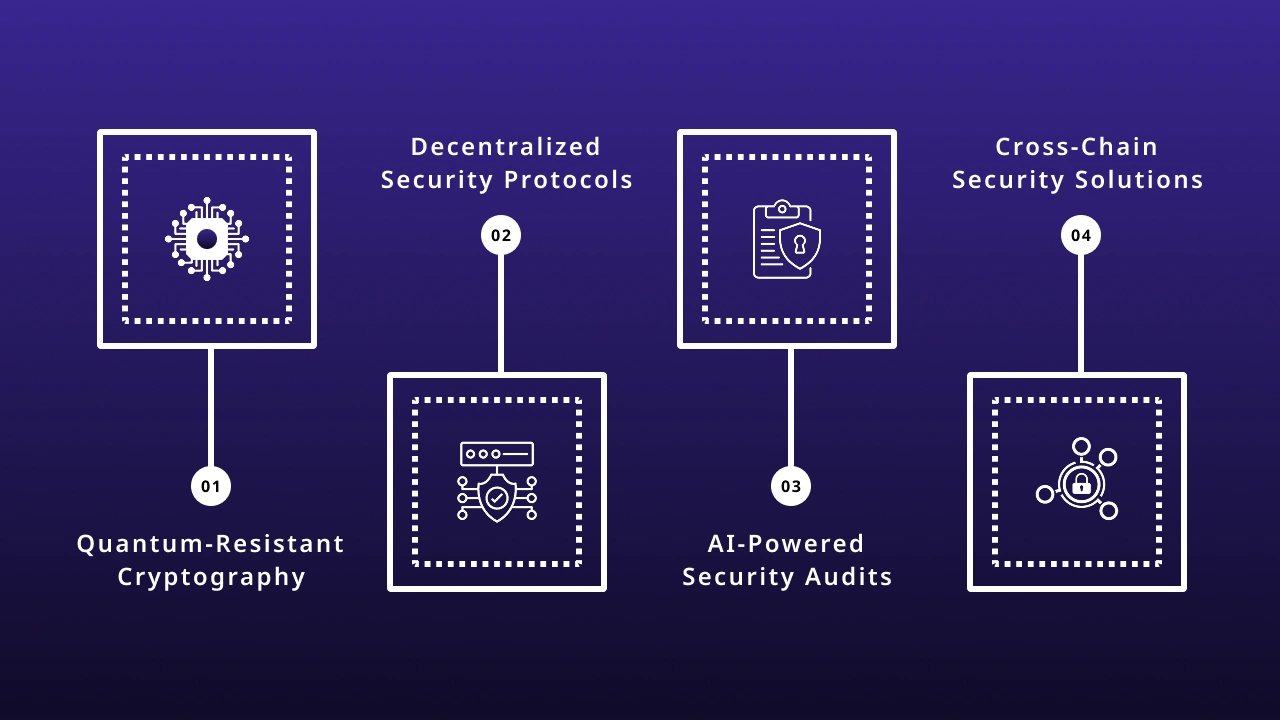
1. Quantum-Resistant Cryptography
Quantum computers threaten current encryption. Future security will rely on quantum-resistant algorithms.
2. Decentralized Security Protocols
Security solutions will become more decentralized, reducing reliance on centralized entities.
3. AI-Powered Security Audits
Automated AI-driven auditing tools will replace manual security checks.
4. Cross-Chain Security Solutions
Interoperability between blockchains will introduce new security challenges, requiring cross-chain security protocols.
Case Studies of Major Web3 Security Breaches
1. The DAO Hack (2016)
A reentrancy vulnerability led to a loss of $60 million in ETH, prompting the Ethereum hard fork.
2. Ronin Network Hack (2022)
An attacker exploited a validator node weakness, stealing over $600 million from the Axie Infinity ecosystem.
3. FTX Collapse (2022)
Although not a hack, the mismanagement of funds highlighted the need for on-chain transparency and proof-of-reserves.
Why True Value Infosoft is the Best Software Development Company
True Value Infosoft has established itself as a Mobile app development company in India by delivering innovative and secure solutions tailored to modern business needs. Here’s why we stand out:
- Expertise in Emerging Technologies: We stay ahead of the curve by adopting and implementing cutting-edge technologies like blockchain, AI, and cybersecurity protocols.
- Client-Centric Approach: Our team prioritizes client requirements, ensuring tailored solutions that drive business growth and efficiency.
- Security-First Mindset: In an era where cyber threats are escalating, we incorporate robust security measures in all our software solutions.
- Innovative Development Strategies: Our development process emphasizes agility, performance, and reliability, making our applications resilient and future-proof.
- Proven Track Record: With a portfolio of successful projects across industries, we have consistently delivered excellence to our clients.
Conclusion
As Web3 continues to evolve, securing digital assets has never been more crucial. By implementing best practices like multi-factor authentication, smart contract auditing, and decentralized identity verification, users can safeguard their assets against emerging threats. True Value Infosoft remains committed to providing innovative and secure solutions, ensuring that businesses and individuals can confidently navigate the decentralized web. Investing in Web3 security today means protecting your assets for the future.
FAQs
Web3 faces several security threats, including phishing attacks, smart contract vulnerabilities, private key theft, and decentralized finance (DeFi) hacks.
Use hardware wallets, enable multi-factor authentication, store recovery phrases securely, and avoid sharing private keys online.
Smart contract auditing is the process of reviewing and testing code for vulnerabilities to prevent exploits and hacks in blockchain applications.
Decentralized identity uses blockchain-based verification methods to enhance security and privacy, reducing reliance on centralized authentication systems.
Businesses handling digital assets must prioritize security to protect their investments, maintain customer trust, and comply with evolving regulatory requirements.





