Introduction
As mobile apps become increasingly essential in our daily lives, ensuring robust security has never been more crucial. With cyber threats evolving rapidly, businesses must adopt cutting-edge security measures to protect user data from breaches, identity theft, and fraud.
In 2025, mobile app security goes beyond simple password protection. It involves advanced encryption, AI-driven threat detection, biometric authentication, and compliance with global security regulations. In this blog, we'll explore best practices for securing mobile apps, real-world case studies, and the future of mobile security.
Why Mobile App Security Matters
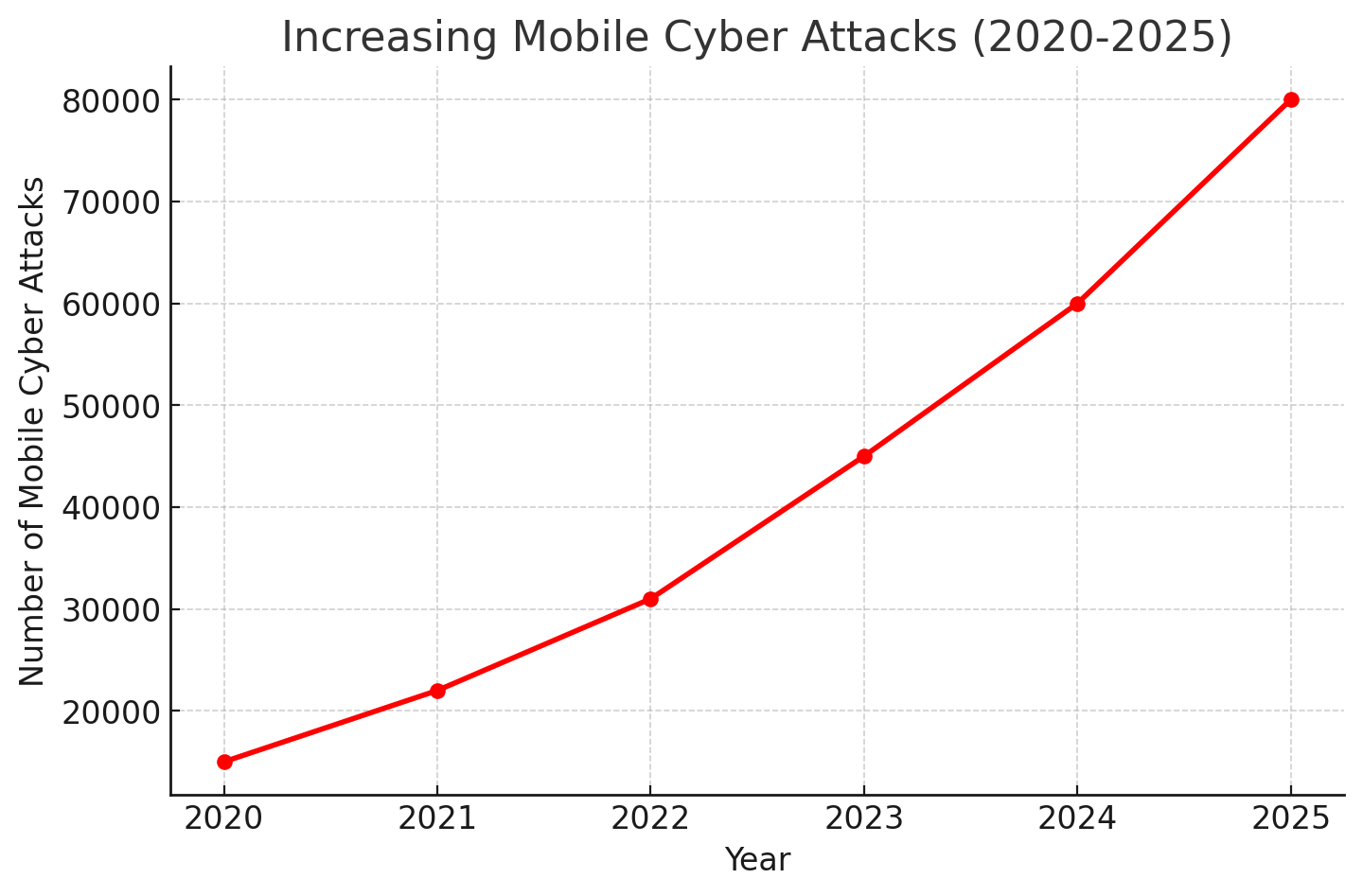
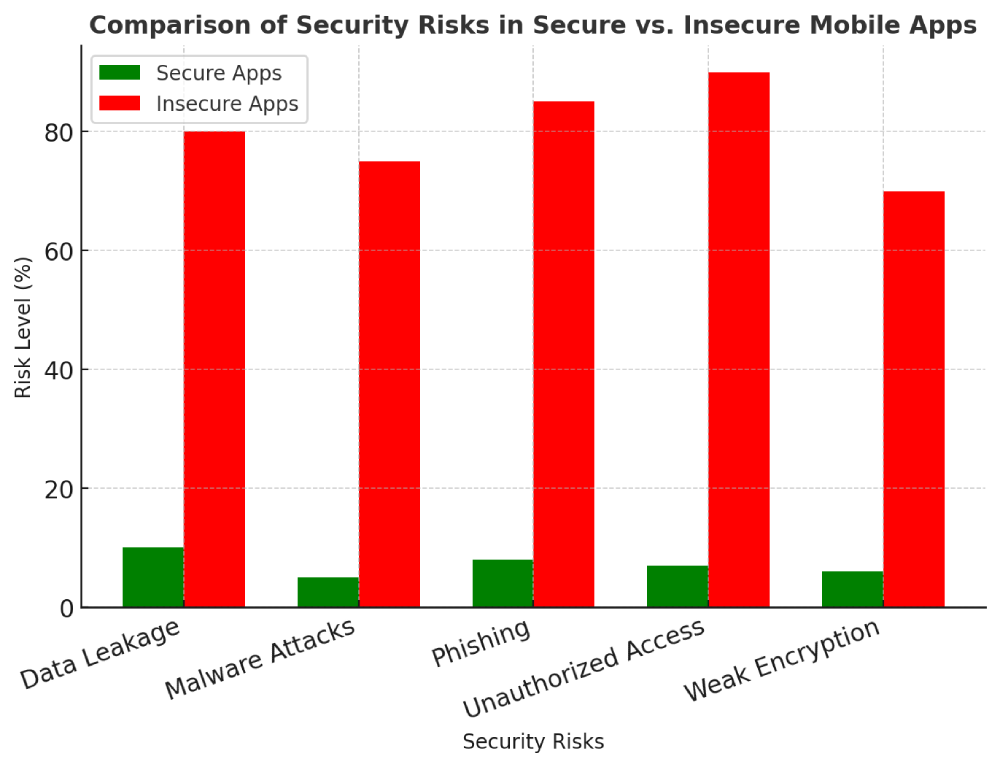
1. Rise in Cyber Threats
Cybercriminals are exploiting vulnerabilities in mobile applications to steal user data, commit financial fraud, and launch ransomware attacks. Without adequate security, sensitive information such as credit card details, personal identifiers, and business data is at risk.
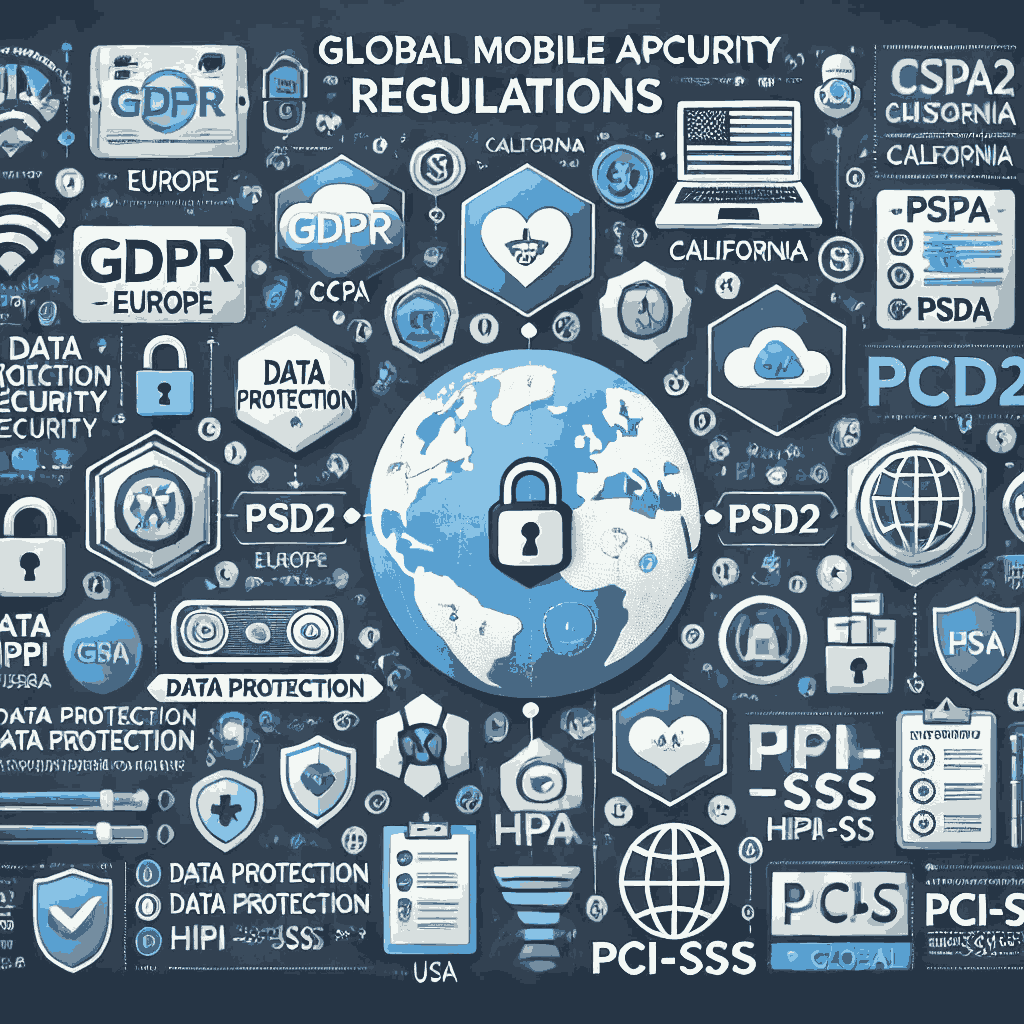
2. Stringent Data Protection Regulations
Laws like GDPR, CCPA, and India's DPDP Act require businesses to implement strong security measures. Failure to comply can result in hefty fines and loss of customer trust.
3. User Trust & Brand Reputation
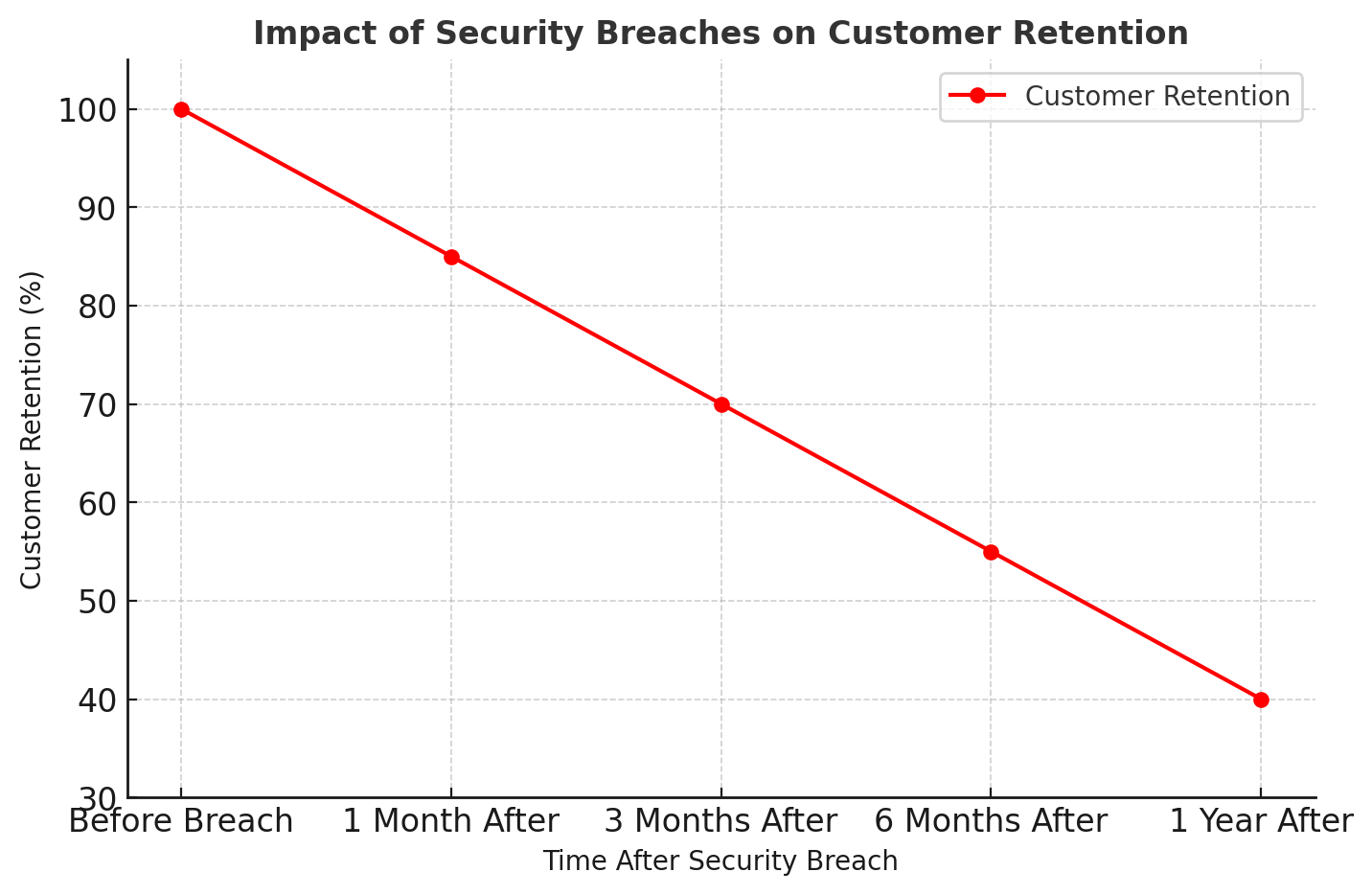
A security breach can cause irreversible damage to a brand's reputation. Companies that prioritize security earn user trust, leading to higher retention rates and increased revenue.
Best Practices for Mobile App Security in 2025
1. Implement Strong Encryption
- Use End-to-End Encryption (E2EE) to protect user data during transmission.
- Encrypt stored data using AES-256 to prevent unauthorized access.
- Secure API communications with TLS 1.3 to block data interception.
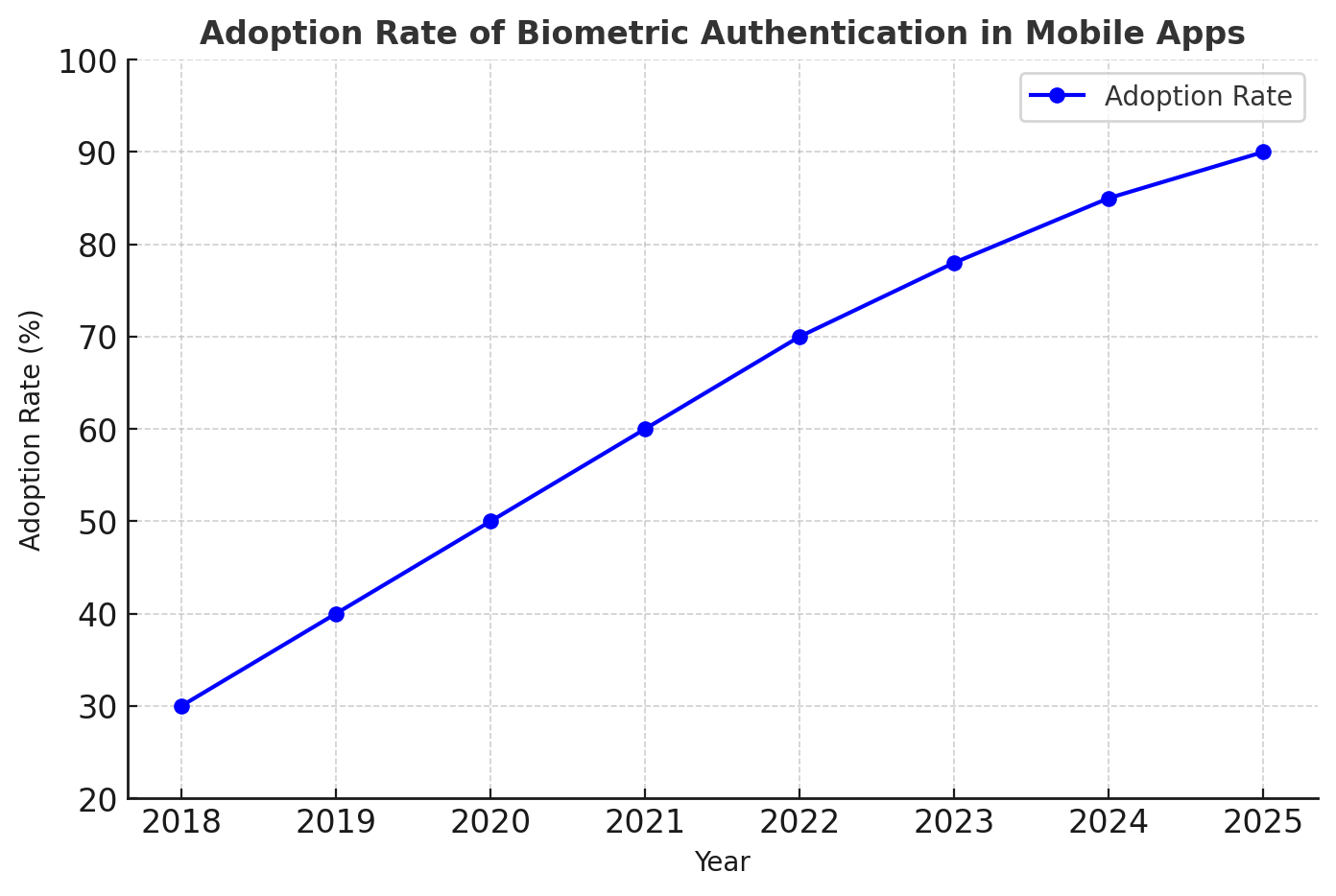
2. Adopt Biometric Authentication
Replacing passwords with fingerprint scans, facial recognition, and iris scanning enhances security while improving user experience. Multi-factor authentication (MFA) adds an extra layer of protection against unauthorized access.
3. Secure APIs Against Attacks
Since most mobile apps rely on APIs, API security is critical. Implement:
- ✔ OAuth 2.0 for secure authentication
- ✔ Rate limiting to prevent API abuse
- ✔ Input validation to mitigate injection attacks
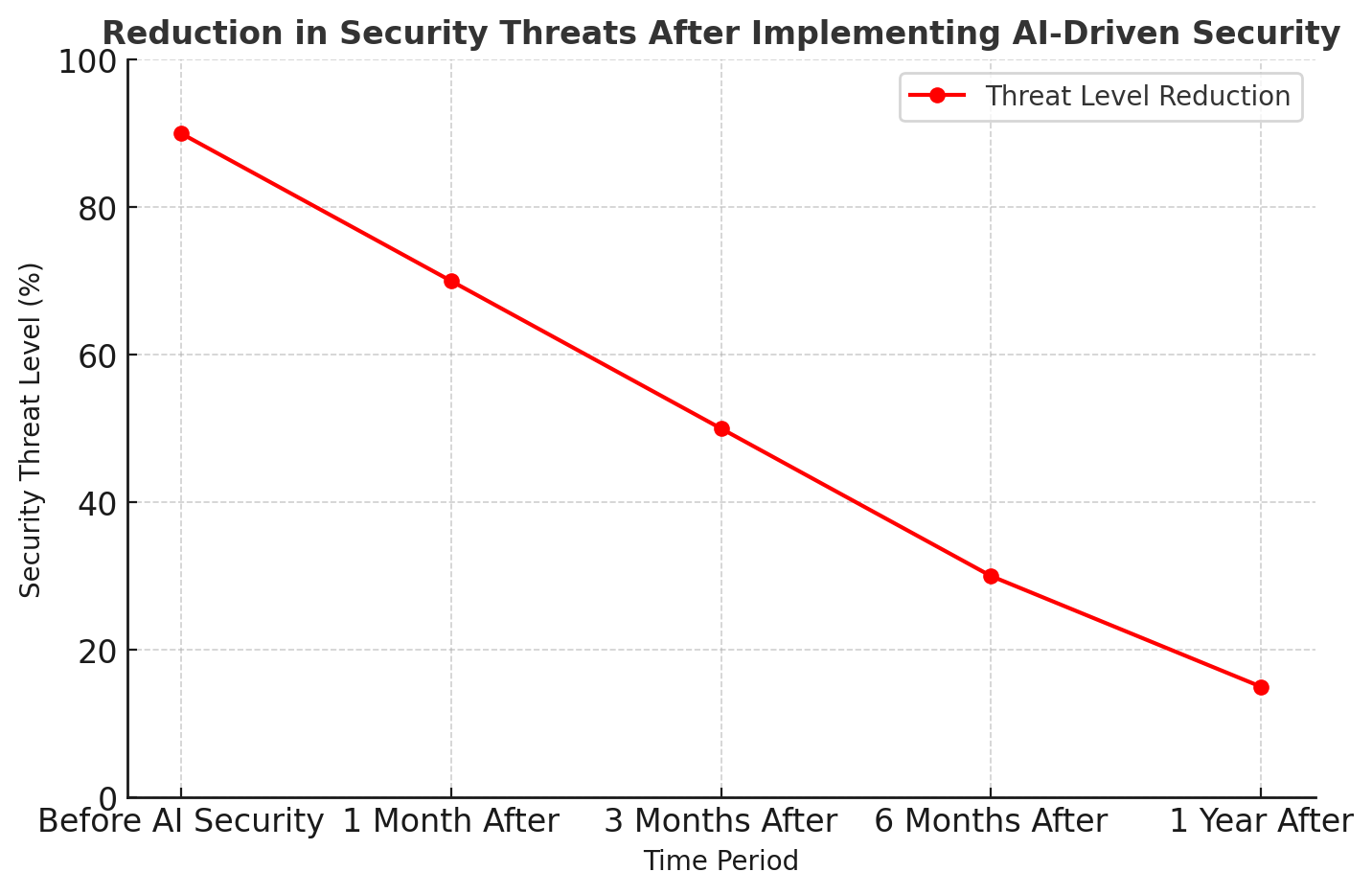
4. Use AI-Powered Threat Detection
Artificial Intelligence (AI) can detect and respond to security threats in real time by analyzing user behavior and identifying anomalies. AI-driven security tools help prevent fraud, phishing attacks, and malware infections.
5. Secure the Code & Perform Regular Penetration Testing
Hackers exploit weaknesses in app code to gain unauthorized access. Protect your app by:
- Using code obfuscation to prevent reverse engineering
- Performing penetration testing to identify vulnerabilities
- Regular security audits to stay ahead of emerging threats
6. Enforce App Permissions & Data Minimization
Apps should only request necessary permissions. Over-permissioned apps increase security risks and violate privacy laws. Best practices include:
- ✔ Requesting only essential permissions (e.g., location, contacts)
- ✔ Minimizing stored user data to reduce breach impact
- ✔ Implementing permission monitoring tools
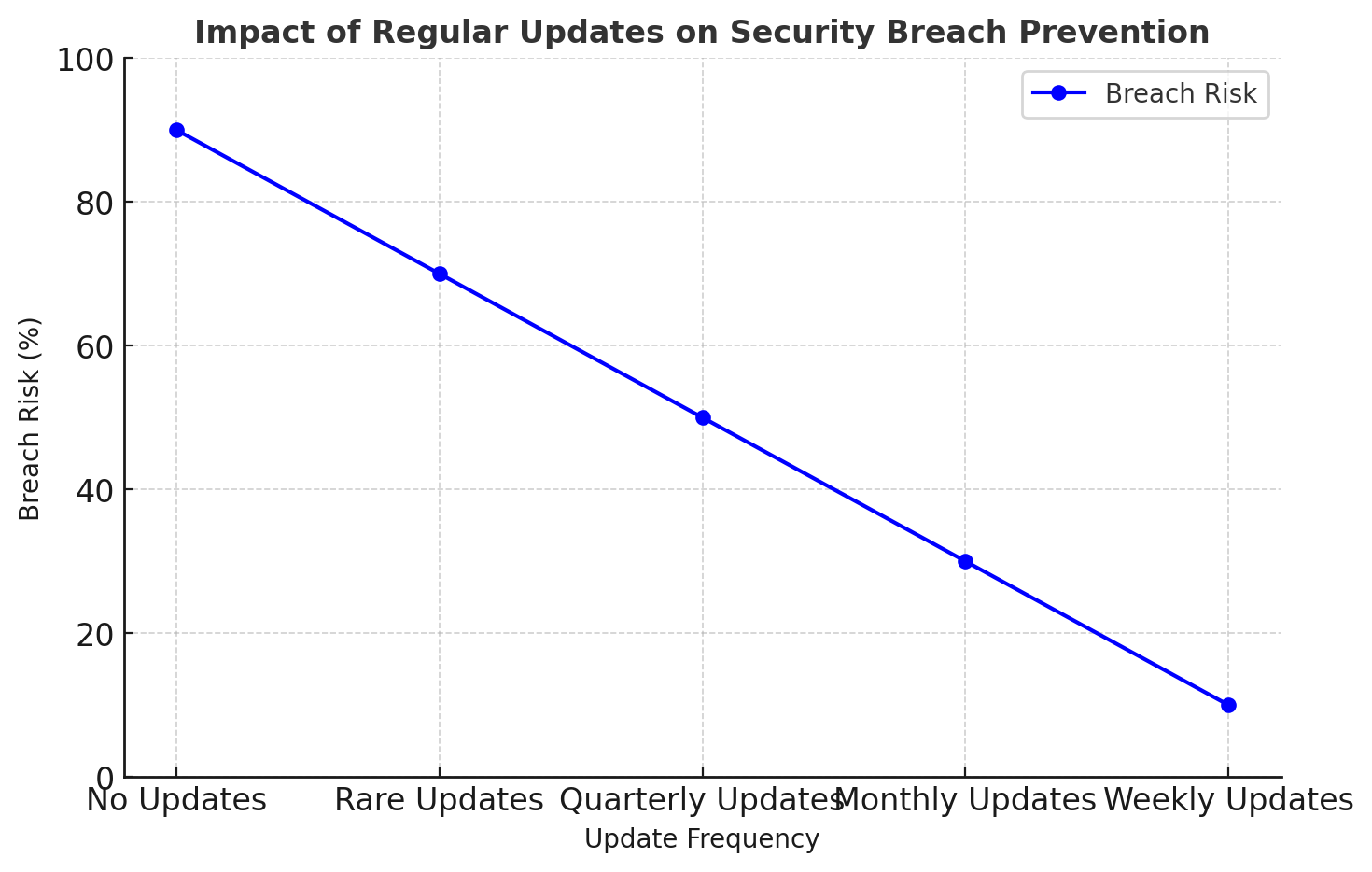
7. Regular Security Updates & Patch Management
Outdated software contains vulnerabilities that hackers exploit. Implement automated patch management to regularly update security patches and fix weaknesses before they are exploited.
Case Study: How a Banking App Prevented a Major Security Breach
Company: XYZ Digital Bank
Problem:
XYZ Digital Bank discovered suspicious login attempts from unknown IP addresses, signaling a potential credential-stuffing attack. Hackers were trying to gain unauthorized access using leaked credentials from a dark web database.
Solution:
- ✅ Implemented AI-driven fraud detection to analyze login behavior
- ✅ Enforced multi-factor authentication (MFA) for all transactions
- ✅ Deployed real-time threat monitoring to block malicious IPs
- ✅ Conducted penetration testing to identify vulnerabilities
Outcome:
- ✔ 99% reduction in fraudulent login attempts
- ✔ No customer data was compromised
- ✔ Improved customer trust and security compliance
- ✔ Increased adoption of biometric authentication
Future of Mobile App Security
- 🔮 Zero Trust Architecture (ZTA): Apps will validate every access request, reducing insider threats.
- 🔮 Decentralized Identity Solutions: Blockchain-powered authentication will replace traditional password-based logins.
- 🔮 Quantum-Resistant Encryption: Preparing for future quantum computing threats with next-gen cryptographic methods.
- 🔮 5G Security Measures: Securing ultra-fast mobile networks to prevent new cyberattack vectors.
Conclusion
In 2025, mobile app security is no longer optional—it’s a necessity. Protecting user data requires implementing strong encryption, biometric authentication, AI-driven threat detection, and continuous security updates. Businesses that prioritize security gain user trust, comply with regulations, and prevent financial losses.
Take action now! Secure your mobile app by following these best practices and stay ahead of evolving cyber threats.
FAQs
The biggest threats include AI-powered cyberattacks, insecure APIs, and credential stuffing. Implementing strong authentication and AI-driven security tools helps mitigate these risks.
Biometric authentication like fingerprints, facial recognition, and iris scans eliminates the need for passwords and prevents unauthorized access.
Apps must follow GDPR (Europe), CCPA (California), DPDP (India), and other regional laws to protect user privacy and avoid hefty fines.
Security testing should be continuous. Regular penetration testing, security audits, and vulnerability scans ensure apps remain protected against new threats.